If You Had to Redesign Unix Again
Delinea Blog > Remember Differently About Unix / Linux Privilege Management
Think Differently About Unix / Linux Privilege Management

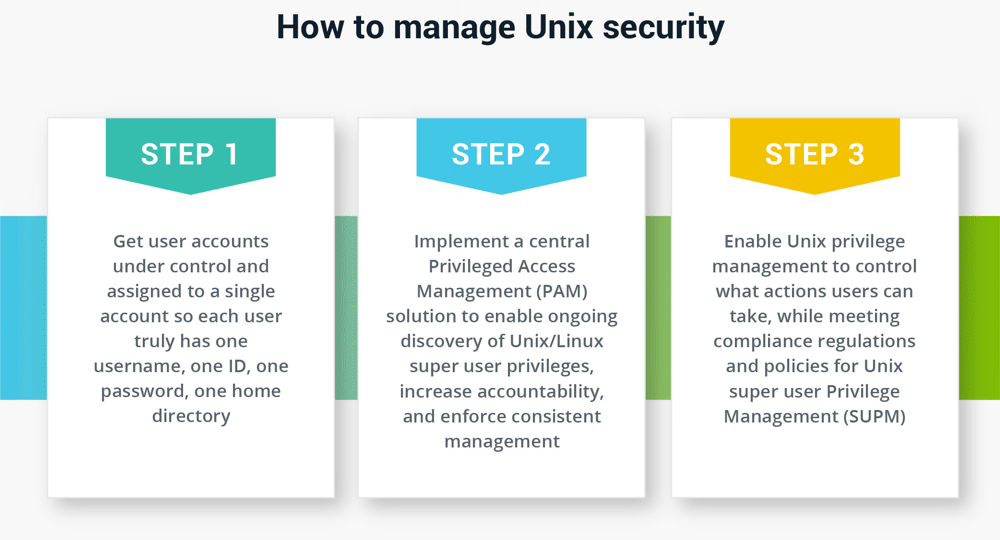
Security models have struggled to friction match the evolution of Unix. Over its long history, Unix has evolved and inverse in many different ways. What started in Bell Labs xl years ago has spawned more 150 variants of Unix in use today. Unlike the linear progression of Windows operating systems, in which most organizations use a single version until it is replaced, many flavors of Unix are in use at the same fourth dimension, even inside a single organization. One thing that hasn't changed much in all these years is that every Unix server, and its open-source cousin Linux, has a local database of users and groups. If y'all take a single host with one user, there'due south no problem with management. But, when yous have multiple servers, a unmarried user becomes multiple and it'south very easy to start mixing things up and create a mess. Yous can easily cease upward with different usernames, UID's, PGID'southward, GID'due south, dwelling directories, login shells, and, of course, passwords on each system. I might be Pharper with a capital P on the first one, pharper on the second, p.harper on the third, so on. With a user'south attributes tied and so tightly to the file and folder permissions on a Unix host, which is something else that hasn't inverse much since the early on days of Unix, user, group, and permission direction quickly becomes a tedious and time-consuming task. It's a lot of work for administrators to go on things secure. Users struggle to remember their credentials and compliance becomes more or less incommunicable. Administrators have turned to numerous different workarounds and configurations to try and ease this burden, with varying success and even so resulting in likewise many local accounts on their organization. Others nonetheless employ generic shared accounts and control privileged access to those shared accounts. This approach is a violation of least privilege best practices and makes it difficult to know who is using the system and what they are doing, which then makes compliance reporting and forensics in the case of a breach quite challenging. Imagine the work when an employee leaves your arrangement Some companies have tried to design and integrate their ain synchronization or provisioning tool, none of which have shown much success. Even those that endeavor to leverage LDAP end upwards with overly complicated configurations and spend many hours managing multiple directories that are split from Agile Directory. You need to assign privileges to users across multiple dissimilar accounts, including LDAP, local accounts, and Active Directory. Just imagine the piece of work when an employee leaves your arrangement and all the places and permutations y'all'd need to cheque to revoke their access. Ignoring the Unix adventure is not an option. If you don't include Unix and Linux in your security strategy, you're leaving open some of the nearly vulnerable and high-value targets prone to attack. Simply put, Unix and Linux systems are high-value targets for cyber criminals. Your mission-critical applications, such as web servers, database servers, and awarding servers, are generally running on Unix/Linux. Linux has now become the most common, go-to operating system for computer hardware and even mainframes these days. It's non just these systems that you must protect; information technology'south the applications and the data stored on them. All Unix and Linux systems suffer from the same weak point – the "root" account. The root account provides the highest and broadest level of command (god-similar privileges), and so protecting root admission must be a priority. In a Unix/Linux environs, many people need or at least merits to need superuser privileges. I have heard the phrase "I demand root" more times than I care to recollect. A user must have superuser privileges for many twenty-four hours-to-mean solar day operations, such as installing, removing, or irresolute whatever piece of software on a given host. A superuser (such as root) has access to the Unix operating system in an unrestricted course and therefore has admission to all commands, files, directories, and resources. Unlike in a Windows or Mac environment, you need to consider privilege direction on Unix and Linux in terms of the control line. The goal of 'command control' is to determine by a policy which commands should be allowed to run and which ones should be explicitly denied. In fact, given the numerous means Unix and Linux let commands to exist issued at the command line, unlike in Windows and Mac environments, choosing which commands or system functions to block is actually more important than choosing which to allow. Privileged session management is another key departure for Unix and Linux security. To monitor and audit privileged business relationship activity on a Windows motorcar, you lot typically perform some course of video screen recording. For Linux and Unix however, you need to log everything the user sees on the screen, specific keystrokes they type, what commands they execute, and fifty-fifty the actions being performed by the system. System-level auditing is important given the amount of administration performed using scripts. Much of the user and superuser changes would exist excluded from the audit trail without such recording capabilities. In one case all this information is gathered, typically in text grade, it should be indexed and made searchable and/or reportable to avert labor-intensive data review processes. Once proper business relationship management has been implemented and y'all've taken steps to secure passwords of privileged accounts (credential and secrets vaulting), then removing all unnecessary access, including straight or break-glass, to accounts such as root should exist the next priority in your Privileged Access Management (PAM) journeying. To address this challenge, Sudo allows Unix and Linux users to run programs with the security privileges of another user. It's basically the equivalent of the "run as" control in Windows. The Sudo method for Unix privilege direction is 30 years erstwhile. It originally stood for "superuser do" equally the older versions of Sudo were designed to run commands only as of the superuser. Later versions of Sudo added support for running commands as other users, so it's at present unremarkably defined as "substitute user do." Sudo provides more fine command than the Unix "Su" command. Su switches you to the root user account and requires the root business relationship's countersign to run. Sudo can run a single command with root privileges. It doesn't switch to the root user or crave a separate root user countersign. The purpose of Sudo is to enforce a to the lowest degree privilege policy, while still allowing you to elevate a user account to have root privileges temporarily. Once a user enters a countersign to provide arrangement-based permissions, the Sudo command provides permissions to whatsoever particular control that a user wants to execute. After authentication, and if the configuration file (policy file/sudoers) provides the user admission, the organisation invokes the requested command with elevated rights. You tin can configure detailed access permissions to increase security controls, such as enabling commands but from the invoking terminal, requiring a password per user or group, requiring re-entry of a password every fourth dimension for a particular control line, permitting or restricting passing arguments, and then on. The flexibility of Unix and the strength of the Linux open up-source customs means you can find many options to enhance privileged security on your own. For example: There are downsides to cobbling together your own Unix or Linux privilege management solution Managing Unix and Linux security on your own is a heavy lift, yet. At that place are many downsides to cobbling together your ain privilege management solution. Unix privilege security is cumbersome and expensive to set. To properly use Sudo, you lot need highly skilled (and highly paid) system administrators to spend a slap-up deal of time edifice sudoers files. Then you have to distribute the files across your arrangement. This privileged security approach is an order of magnitude more difficult to maintain when new versions of Unix or Linux are adopted by your users. Even afterward you consummate the initial setup, doing everything yourself means you accept no vendor to rely on for testing, maintaining, documenting, and other ongoing software management functions. In improver to administrative and operational costs, there are too security and compliance risks with the typical approach to privileged security for Unix and Linux: If yous don't maintain and update Sudo, you may miss security vulnerabilities. Just last year, developers fixed a flaw in Sudo that let you lot claim root-level access fifty-fifty if the configuration explicitly forbids it. If an intruder had enough access to run Sudo, they could perform whatsoever activity they wanted on a given machine. Nosotros believe it's time to retrieve differently most how to manage Unix security. A multi-layered arroyo simplifies direction and reduces security risk. We recommend the following arroyo: Step 1 The first order of business for Unix protection is to become everything in i place. To manage Unix security in a sustainable manner, yous need to become user accounts under control and assigned to a single account. In a Windows environment, Active Directory (Advertising) allows this unification. AD leverages LDAP under the hood, simply information technology largely uses Kerberos as the authentication protocol for Windows machines, and so Unix devices struggle to integrate with AD. An AD bridge extends Group Policy to non-Windows platforms and then you can perform account maintenance and password updates for all systems through a single tool. With an Identity Bridge, you take advantage of consistent data across all of your systems. Each user truly has ane username, one ID, i password, one home directory, etc. Stride 2 Once this type of identity unification is in place, a central PAM solution connects to your AD and lets yous authenticate users and assign privileges with ease. PAM solutions enable the ongoing discovery of Unix/Linux superuser privileges to increase accountability and enforce consistent management. Immutable inspect trails and enhanced controls, such equally session monitoring and recording, provide oversight and simplify reporting and compliance. Step iii After a user is authenticated and logged in to your IT resources, Unix privilege management controls what actions they tin can take. Granular control of root credentials limits privileges while coming together compliance regulations and policies for Unix Superuser Privilege Management (SUPM). You tin can reduce the risk of privileged account abuse or adventitious error by restricting commands based on defined policies and limited superuser permissions. SSH command allowlist allows admins to log in equally root, but only gives them access to a set of predefined commands. For case, a Unix allowlist might mean Information technology administrators might be able to restart the database and read log files, but not reset user passwords. Most organizations have a mix of different operating systems for different functions. Some teams volition always prefer Unix and Linux to Windows or Mac due to their flexibility also as their open-source nature. Every bit a security leader, you need to include all types of IT systems and all parts of your organization in your security strategy and ensure they follow security policies consistently. You can back up the different operating system groups within your Information technology arrangement and manage a comprehensive privileged security strategy with advanced least privilege solutions. Users like this approach considering they no longer accept to remember multiple credentials to log onto each of their systems. A cardinal PAM solution reduces the run a risk and complexity of managing a heterogeneous environs. It provides the do good of common security policies and practices across groups. Preparing reports for management and audits become a simple, repeatable procedure. Now, when you demand to revoke access when an employee leaves your arrangement, yous can manage information technology with i step and include all systems. Talk with our squad virtually Delinea and Unix / Linux privileged management and stay tuned equally we continue to gyre out solutions for each step in a layered approach to Unix protection.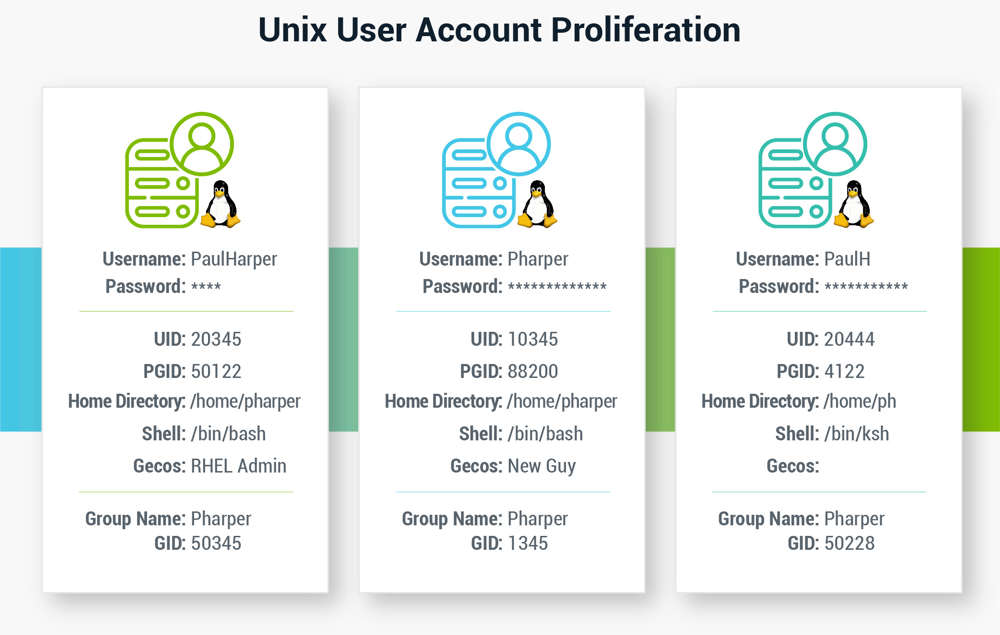
Why should you focus on Unix and Linux security?
Unix/Linux privilege management is different from Windows and Mac
The typical method of Unix/Linux privilege management and privilege elevation is Sudo
A sophisticated Unix team can add together privileged security functionality to basic Unix protections
Comprehensive, enterprise PAM is a meliorate solution for Unix/Linux protection
Benefits of a unified privilege management/PAM organisation for Windows, Mac, and Unix
Source: https://delinea.com/blog/unix-linux-privilege-management
0 Response to "If You Had to Redesign Unix Again"
ارسال یک نظر